What is Digital signature standard?
Updated on : 2020-Nov-19 13:28:22 | Author :
Contents
- Introduction
- Revisions, Applications, and Implementations of DSS
- Digital signature standard or DSS
Introduction
Digital Signature Standard (DSS) is one kind of federal information processing standard. It specifies a set of algorithms that are used to generate digital signatures that are introduced to us by the US National Institute of Standards and Technology(NIST) in the year 1994. It is the Digital Signature Algorithm can be used for the authentication of electronic documents. Digital Signature Standard is the specific federal information processing unit 186.
-
Category of the standard: Computer security
-
Subcategory of the standard: Cryptography
-
Establishment of Digital Signature Standard
Digital Signature Standard (DSS) was established in the US. National Security Agency (NSA) played a key role in introducing the Digital Signature Standard. It was put forward by the US National Institute of Standards and Technology (NIST) in the year 1994. It has turned out to be the United States Government Standard to authenticate electronic documents.
Revisions, Applications & Implementations of Digital Signature Standard
Revisions
There are a total of four revisions have been delivered to the initial specification. They are-
· FIPS 186-1 in 1996
· FIPS 186-2 in 2000
· FIPS 186-3 in 2009
· FIPS 186-4 in 2013
Application
It enables the authentication of the signatory. As a result, data integrity is enclosed. Digital Signature Standard is used to generate Digital Signatures. It is also used to verify it. It is used to find out the unauthorized modifications made to data and to authenticate the identity of the particular signatory. It applies to all federal departments and agencies to protect sensitive and unclassified information. This Digital signature standard must be used in the activities of designing and implementing the uses of public key an abased signature function that the federal departments and agencies manage or which are managed for them under the contract.
Implementation
The Digital Signature Standard may be implemented in the software, firmware, hardware, or in any combination of the following. Agencies are advised that the key pairs of a digital signature shall not be used for other purposes except the mentioned one. Every signatory has its own set of public and private keys. Information about the Private and Public keys are as follows-
Digital signature standard or DSS
Private Keys
Only the user knows this private key.
Public Keys
The public keys are considered to be known by the general public.
Approach
The Digital Signature Standard is designed to simplify the Digital Signature Facility. It cannot be used to encrypt or exchange keys. It is a technique of public key. It uses the Hash function. The Hash code is provided to act as an input to a signature facility together with a random number k generated for this specific signature. The signature function depends on the private key of the user or sender. Then a group of parameters is known to a group of communicating principals. The Private key set constitutes a general Public key. The Hash code of the incoming message is generated at the receiver end. A verification function takes place. The verification depends on the general public key and the sender’s public key that is paired with the sender’s private key.
- It is fixed in a FIPS
- It is taken in a FIPS or NIST recommendation or
- It is specified in the list of approved security functions for FIPS 140
Creating a digital signature using the digital signature standard
The following flowchart represents the process of creating a digital signature using the digital signature standard-
Benefits
The recipient of the signed data can freely use a digital signature as evidence to demonstrate to a third party that the signature was generated by the claimed signatory. This is known as non-repudiation as the signatory is unable to easily to repudiate the signature later.
Export Control
Cryptographic devices and technical data are the subjects of the federal export controls. These must comply with the federal regulations and be licensed by the Bureau of Industry and Security of the US Department of commerce.
Patents
The algorithms of this digital signature standard may be covered by the patents of the US or Foreign countries.
- Category of the standard: computer security
- Subcategory of the standard: Cryptography
- Approving authority: Security committee
- Maintenance Agency: Department of Commerce, NIST & ITL & computer security divisions.
Applicability
This DIGITAL SIGNATURE STANDARD generally applies to all the Federal dept.s and agencies for the protection of sensitive unclassified data that are not subject to section 2315 ( Title 10), the united states Code, or section 3502 (2) of Title 44 Code. This digital signature standard shall be utilized in the planning and implementing the public key-based signature systems that the Federal departments and agencies operate or which are operated for them under the contract. The adoption and usage of this digital signature standard are out there for private and business organizations.
Application
A digital signature algorithm system permits an entity to demonstrate the intact integrity of the signed information and therefore the identity of the individual. The recipient of a signed message will use a digital signature as proof in demonstrating to a 3rd party that the signature was generated by the claimed individual. this can be called non-repudiation since the individual cannot simply repudiate the signature at a later time. A digital signature the formula is meant to be used in electronic mail, electronic funds transfer, electronic information interchange, computer code distribution, information storage, and alternative applications that need information integrity assurance and information origin authentication. Implementations: A digital signature algorithm could also be enforced in computer code, firmware, hardware, or any combination thereof. National Institute of standards and Technology |NIST agency |federal agency| government agency |bureau |office |authority has developed a validation program to check implementations for conformity to the algorithms during this Standard.
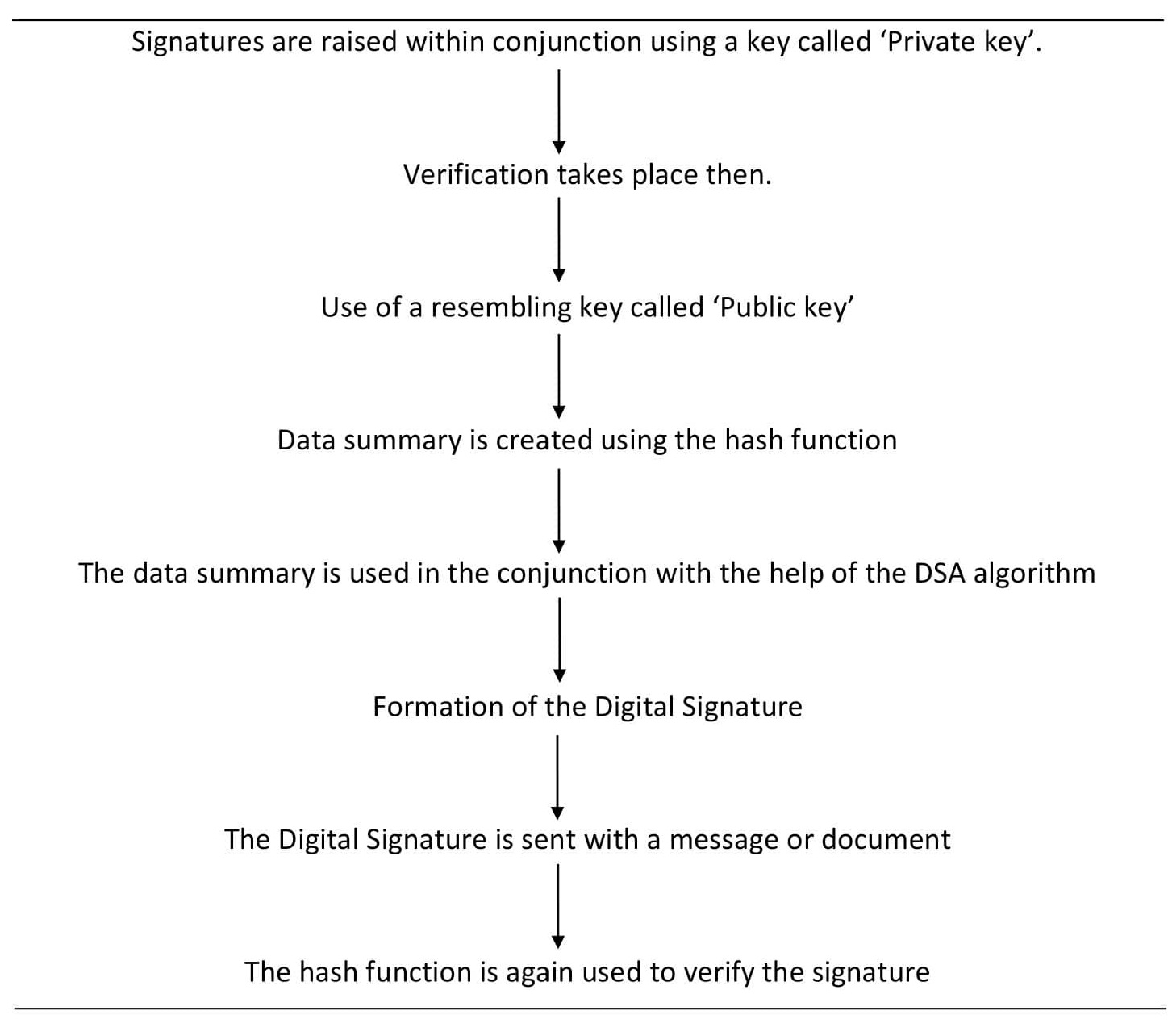
How digital signature standard is used to get a digital signature?
The digital signature standard follows the following methods-
1. Signatures are raised within conjunction using a key called ‘Private key’.
2. Verification takes place then.
3. Use of a resembling key called ‘Public key’
4. Data summary is created using the hash function
5. The data summary is used with the help of the DSA algorithm
6. Formation of the Digital Signature
7. The Digital Signature is sent with a message or document
8. The hash function is again used to verify the signature
Additional resources
- https://lenstax.com/l/process-and-how-to-create-digital-signature
- https://lenstax.com/l/digital-signature-certificate-faqs
- https://lenstax.com/l/digital-signature-certificate-or-dsc-at-a-glance
- https://lenstax.com/l/process-of-getting-digital-signature-certificate-dsc
- https://lenstax.com/l/digital-signature-digital-signature-certificate-dsc
- https://lenstax.com/l/digital-signature-algorithm-dsa


